How does Cyber Criminals Spear Phish you?
- Cyber Criminals will scan thru internet and target business that
- Multiple presence globally
- Have overseas customers
- Have overseas suppliers
- Doing regular bank transfer payment
- From your website, study your nature of your business
- Thru social engineering, ask for the finance/accounts key person's email address
- Thru social media like Facebook, LinkedIn, study how to target the key person.
- From the domain information, the cyber criminal can know whether the user is a Google, Office 365 or Domain Registrar POP/IMAP Mail Hosting
- Obtain the key person email password by directing you to go to the fake website to authenticate identity and password.
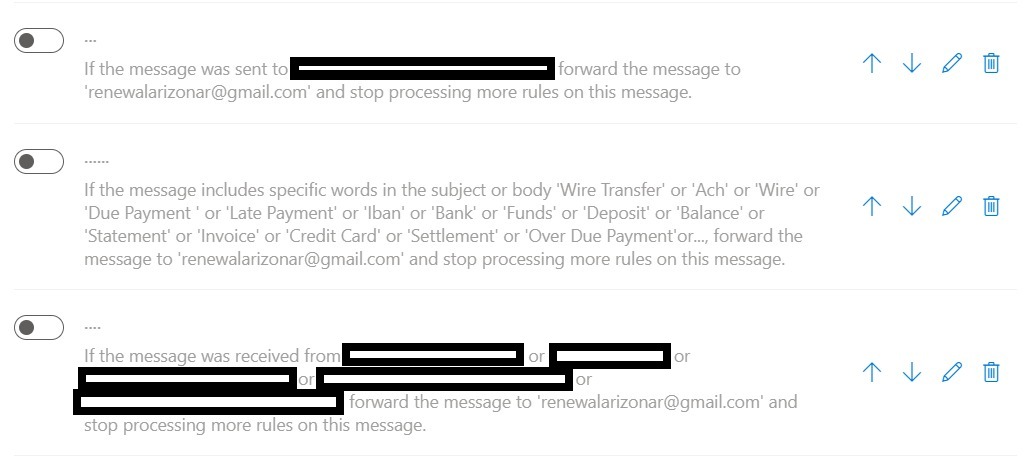
- After obtaining the mail login credentials, login to webmail and setup 3 forwarding email rules to monitor your activities silently (See Below)
- Email that has certain keywords in the subject or body like "late payment", "wire transfer", "due payment" and so on (See Below)
- to identify potential victim
- Email sending "TO" certain email address of the potential victim
- to monitor, analyse and plan for the right time to strike
- Email receiving "FROM" certain email address of the potential victim
- to monitor, analyse and plan for the right time to strike
- Buy a suitable similiar domain name under a fake identity
- Send email phishing to the targeted email address (planning for the next victim)
- Send spear phishing (phase 1) to the targeted email address to remind on upcoming payment
- Send spear phishing (phase 2) to the targeted email address to follow up on upcoming payment
- Send spear phishing (phase 3) to the targeted email address requesting for a change in bank account and to make a bank transfer
For Office 365 users
- In a web browser, sign in to Outlook Web App using the URL provided by the person who manages email for your organization. Enter your user name and password, and then select Sign in.
- At the top of the page, select Settings > Options.
- In Options, select Organize email > Inbox rules.
For Google users
- Login to Gmail
- Near the top right, select the Gear Icon and click on "Settings"
- Select "Filters and Block addresses"
- Go thru the rules
Over the years, cyber criminals have learnt how to monetize their criminal activities. It is so amazingly well structured and highly automated as well.
Are You in High Risk Group?
- Your domain is using .com or .net
- .com.sg or .sg are safer as you will need a SingPass to register these domain
- If your domain has these letters
- g → q
- m → rn (r & n)
- n → ri (r & i)
- i → 1 (numeric 1)
- w → vv (2 v)
- d → cl (c & numeric l)
- Multiple presence globally
- Have overseas customers
- Have overseas suppliers
- Doing regular bank transfer payment
- Do not have Endpoint Security
- Do not have secure VPN/2FA
- Use android phones
- Do not change password regularly
- Access webmail on public and friends PC/Notebook
- Your email might be compromised - You can check here https://haveibeenpwned.com/
Related Topics :



Comments
Post a Comment